
Apple has pushed out an urgent software update to users of iOS and macOS after discovering a vulnerability that could target holders of cryptocurrencies.
According to Kaspersky, Apple has released urgent updates due to vulnerabilities in iOS and macOS devices. The security firm urges Apple users to update devices to iOS 16.4.1 and macOS 13.3.1.
Due to the security weakness, bad actors can “do almost anything,” even steal crypto from their targeted devices.
How Are Apple Devices Vulnerable to Crypto Hacks?
Apple recognized two security threats, CVE-2023-28205CVE-2023-28206, a combination of which can allow exploiters to conduct zero-click exploits. This is an attack where victims are taken to phishing websites, and malware is automatically installed inside their devices without interacting with the page.
After installing malware, attackers can control the device and run codes without the need for the operating system’s core permissions. They might even access cryptocurrency wallets present on users’ devices.
Rising Crypto Phishing Attacks
Phishing attacks are gradually becoming a favorite mode of cryptocurrency hackers to steal users’ funds. According to a Kaspersky report, cryptocurrency phishing by 40%, from 3,596,437 in 2021 to 5,040,520 detections in 2022.
Generally, phishing websites slightly differ in spelling, which is hard to spot for unaware users. They trick victims into connecting wallets and then drain out the assets, including crypto tokens and non-fungible tokens (
Certain bad actors also run Google Ads to display their phishing websites on the top of the search page. BeInCrypto reported that Google showed a fake CoinMarketCap link above the original website in October.
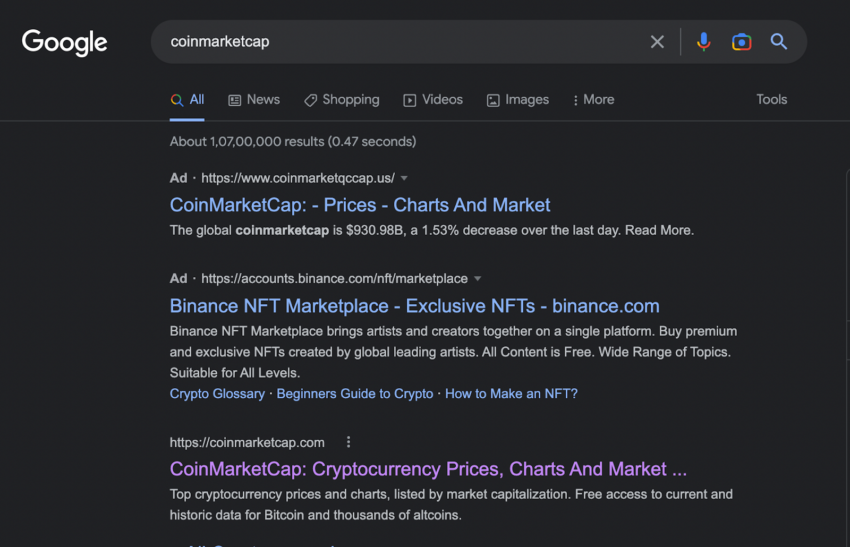
Moreover, according to a survey of 2,000 Americans, one-third of respondents have been victims of crypto theft.
Hence, users should take security measures such as diversifying funds in different wallets and securely storing private keys. On top of that, users should thoroughly evaluate the authenticity before clicking on a link.
Got something to say about Apple devices’ vulnerability or anything else? Write to us or join the discussion on our Telegram channel. You can also catch us on FacebookTwitter











